Advanced Security Solution
What is a SOC?
A security operations centre (SOC) is a centralized hub or command centre that augments your overall IT & data security defence posture by harnessing the collective power of technology, processes, and people to aggregate, analyze, support, and manage the multiple security measures in place to protect your organisation.
Comprehensive Security Defense. Offering you advanced security controls. Retains logs for 12 months.
Key Features:
24x7 Detection & Response
- Windows & MAC OS
- Event logs, advanced breach detection/isolations & threat hunting
- Edge Devices, Systems and Firewalls
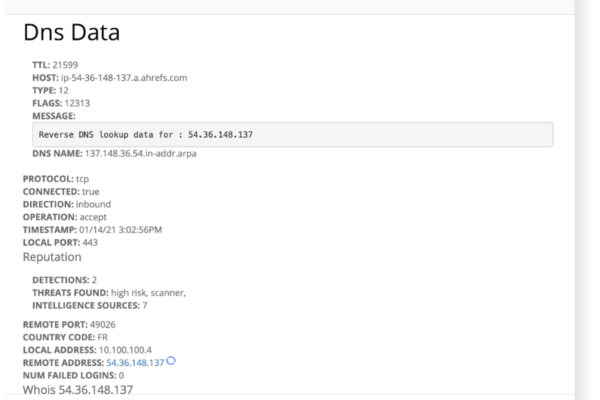
- DNS, WHOIS, Threat reputation investigations and monitoring
- Microsoft 365 & AzureAD
- Event log analysis and monitoring of Active Directory access and activities
- Monitor & Identify Malicious logins or anomalous behaviors or changes
Advanced Security for Microsoft 365 & Azure AD
The largest security gap and blind spot for threats = Email
- We monitor your O365 accounts for business email compromises (BEC), unauthorized rule forwarding, and excess privileges risking data leakage.
- We monitor the Dark Web 24×7 for any exposed credentials linked to your domain or IP details
Increased Visibility & Control Permissions & Access in Active Directory
- Track and observe all event log activities within your Azure AD account for malicious logins or suspicious/anomalous behaviors or changes indicating potential security breach threats.
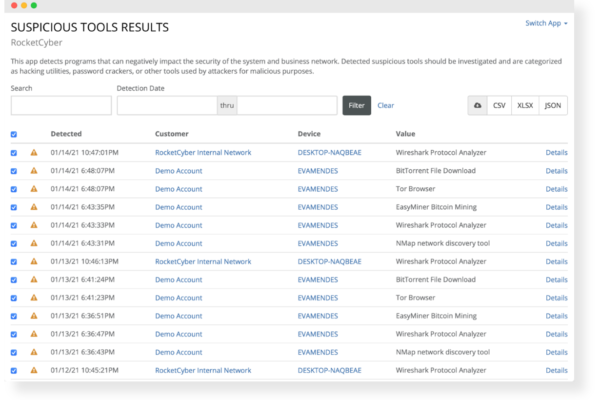
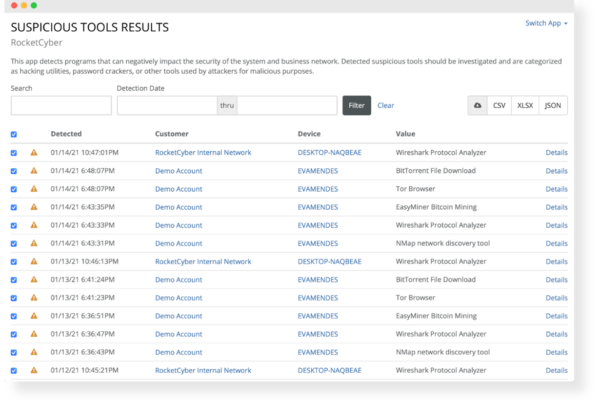
Detect Suspicious Tools & Programs
This app detects programs that can negatively impact the security of the system and business network. Detected suspicious tools should be investigated and are categorized as hacking utilities, password crackers, or other tools used for malicious purposes
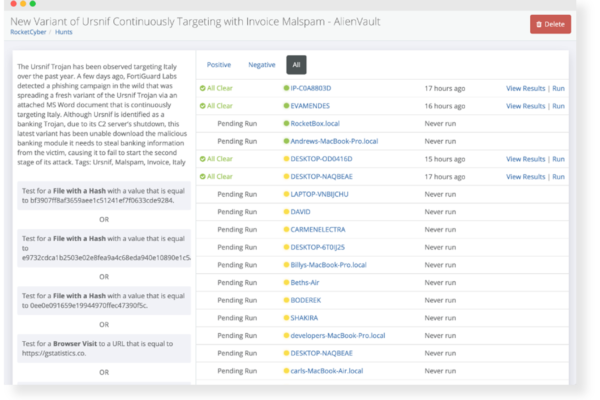
Real-time Threat Hunting and Investigations
Activities and alert messages are aggregated, parsed, and investigated to identify potential threat indicators. We can detect suspicious tools that should not be present on your network, such as hacking utilities, password crackers, etc. used for malicious intent.
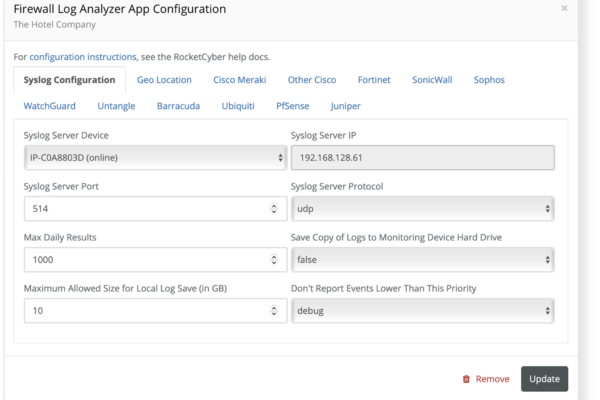
Monitor & Track Firewall Logs
We monitor firewall logs acting as a syslog collector. Activities and alert messages are then aggregated, parsed, and investigated to identify potential threat indicators.
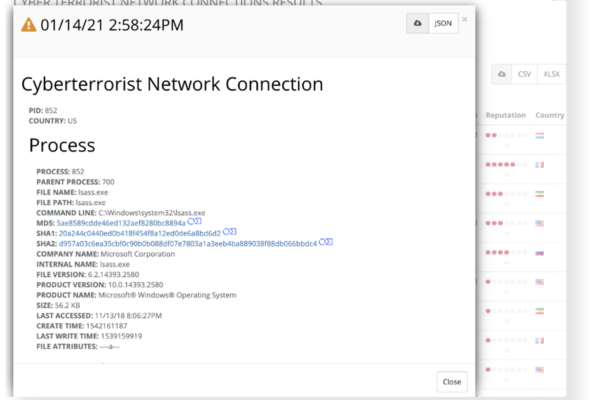
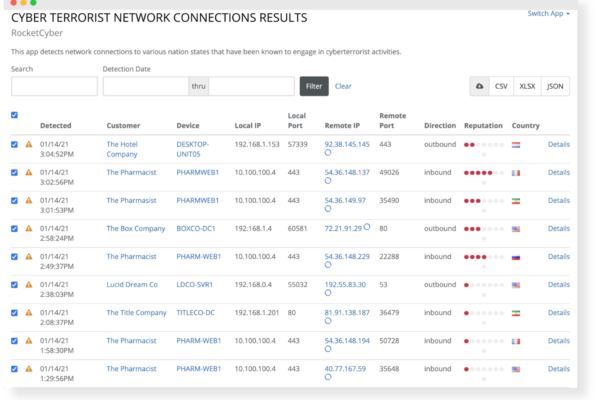
Cyber Terrorist Network Connections
This app detects network connections to nation states that are known to engage in cyberterrorist activities targeting small businesses.
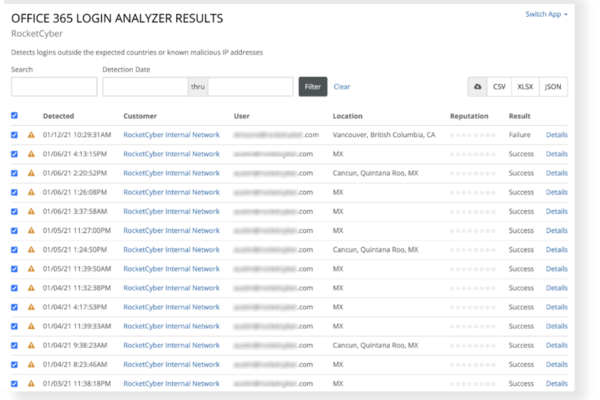
Enhanced Visibility into Email Threats
Using Office 365 log monitor and Office 365 login analyzer to detect and alert any suspicious emails which show signs of phishing, baiting, ransomware, etc.
DNS Filter Monitoring
Using Office 365 log monitor and Office 365 login analyzer to detect and alert any suspicious emails which show signs of phishing, baiting, ransomware, etc.
Crypto Mining Detection
Monitors for Cryptojacking, the unauthorized use of a computer to mine cryptocurrency. Detects for endpoint presence and in-browser javascript miners. Cryptojacking occurs when a miner client is downloaded to a system or by visiting a website with an embedded javascript miner.
While the impact of stealing computing power is causing a rise in electricity bills, bandwidth consumption and the slow down of computer resources, it has become a new vehicle for attackers to deliver ransomware, malware and creation of backdoors. When crypto miners are detected, you have the option of sending alerts to your PSA, receiving email notifications and/or generating white labeled reports.