Email security has evolved
Email is the most used application by both organisation’s and cybercriminals, enabling malware delivery, phishing, impersonation attacks, and the spread of internal cyber threats to your organisation. Methods of attack are changing rapidly and growing to be more sophisticated, targeted, and dangerous.
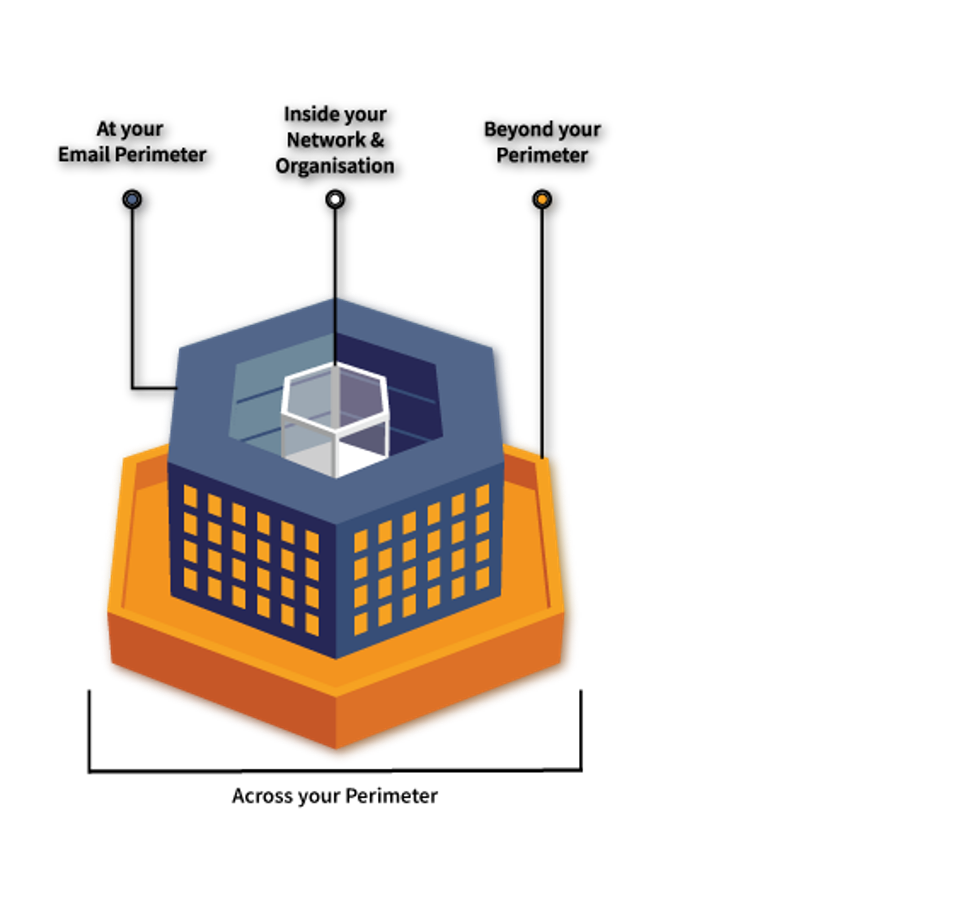
Mimecast email security is a comprehensive cloud-based email security and compliance solution. Their extensible mail transfer agent (MTA) with its multiple layers of malware and spam protection acts as your email secure ground in the cloud, blocking known and emerging email threats before they reach your network.

Mimecast is dealing with email security challenges of today at industry scale with Email Security 3.0. The technology is built with a premeditated and scalable design that benefits you to achieve greater security whilst reducing cost and intricacy.
Mimecast’s Email Security Approach
For more information:
Enquire now:
